Protect Stevens Program
Technology impacts nearly all aspects of our professional and personal lives today, and our user accounts are the basic mechanisms that safeguard our online access. It is vitally important to realize these two basic facts: Everyone is the target of hackers, and no one is immune from cyberattacks. The Division of Information Technology has compiled this page to provide education on protecting yourself from these cyberattacks. Also, please reference Stevens security policies on our Governance, Policy & Standards page for further guidance.
The State of Cybersecurity at Stevens
Hear from Jeremy Livingston, Chief Information Security Officer, and Michael Parente, VP for Information Technology and Chief Information Officer, as they provide an update on our Cybersecurity Program “Protect Stevens”. Learn about our goals for managing the risk to and security of the university's IT resources and those they represent.
Security Links
- Alumni Accounts and Email Forwarding
- Guide to Data Security and Protection in AI Tools
- Critical System Intake Process
- Digital Copyright and DMCA
- Endpoint Protection and Management
- European Union General Data Protection Regulation (GDPR) FAQ
- Identity and Access Management
- Identity Theft Program
- Information Security Policy
- Information Security Policy Appendix A
- Information Security Policy Appendix B
- Internal Guidance - DOJ Data Security Programs
- Local Administrator Rights and Processes & Requests
- Privacy Policy
- Stevens Gramm Leach Bliley (GLB) Act Information Security Plan
- Traveling to High-Risk Countries
Tips for Staying Safe Online
Scam Awareness
Recently there has been an uptick in scams targeting the higher education community. While these tactics are not new, they are constantly adapting to catch more victims off-guard for nefarious purposes. Such scams can include, but are not limited to:
Financial Aid/Scholarship Scams
Job Offer Scams
Tuition Scams
Fake Check Scams
Credit Card Scams
Public Wi-Fi Scams
Fake Apartment Scams
Social Media Scams
Do
Be cautious about clicking links or downloading attachments in email, text, or social media messages, even from someone you know.
Be wary of unsolicited emails regarding job applications to which you have not applied or are too good to be true.
Consider using a VPN when using a public Wi-Fi network.
Consider using a password manager, such as LastPass, to protect your accounts.
Report suspicious emails by using the “Report Phishing” button in outlook.
Do not
Send payments via gift cards or cryptocurrency.
Agree to any monetary assistance without proper research (jobs, debt relief, tuition, etc.).
Answer messages through email, text, or social media asking for money, personal or financial information.
Fall for the newest scams (read more in our Security Bulletin below) and make sure you report scams
Protecting Your Account and Credentials
Do
Lock your computer if you walk away from it.
Use caution when choosing to save your login information in browsers such as Google Chrome or Mozilla Firefox – if your laptop is lost or stolen, someone who can access your computer can access your accounts. Consider using a password manager, such as LastPass.
Do not
Share your password with anyone else – you are responsible for your account.
Fall victim to phishing or spear-phishing attempts.
Checking Your Accounts Periodically
If at any point you have reason to believe any of your accounts could have been accessed inappropriately, please contact the appropriate party immediately (call your bank if there are suspicious activities, etc.).
Check your information related to that account to make sure nothing has been changed unless legitimately by you:
Email messages, including any sent emails you do not recognize.
Employee information in Workday such as beneficiaries, direct deposit information, dependents, and similar important data.
Retirement account information such as TIAA accounts.
Online bank accounts as well as your credit history and scores.
Important files on your computer or network file shares.
Any other sources you might normally access.
If you detect any problems with your Stevens-related accounts, please contact the appropriate office immediately (for example, the Division of Human Resources, Payroll Office, Division of Information Technology, etc.).
Other Available Options
Antivirus software (available to Stevens students, faculty, and staff for personal use).
Password management software such as LastPass.
Home Internet Security course, powered by KnowBe4, available to Stevens students for free.
Identity theft protection such as LifeLock or TrueIdentity.
Remember:
Loss of data, causing harm to employees, students, and yourself.
Financial losses, including your accounts, loss of confidentiality and security, and the possibility of identity theft.
Malware downloaded to your computer, and possibly to Stevens systems and other members of the Stevens community.
NOTE: TO ENSURE YOUR SAFETY AND THAT OF STEVENS FOR OUR STUDENTS AND OTHER EMPLOYEES, ANY ACCOUNT THAT IS SUSPECTED OF BEING COMPROMISED WILL BE LOCKED UNTIL THE OWNER IS CONTACTED, THE PASSWORD FOR THAT ACCOUNT IS CHANGED, AND INTEGRITY OF THE ACCOUNT IS REESTABLISHED.
Mobile Devices
Best Practices for Securing Mobile Devices
Mobile devices refer to smart phones, tablets, and e-readers. Users with mobile devices that are either Stevens-managed or personally managed need to ensure the following:
Use a strong passcode to lock your device. Consider using biometrics authentication (e.g., fingerprint, face) for convenient data protection.
Update your operating system regularly. For convenience, consider turning on automatic software updates.
Do not jailbreak/root your mobile device. You may stop receiving important security updates and the device will become more vulnerable.
Enable encryption on your mobile device. iPhone and Android have built-in encryption, and enablement options can be found in the device settings.
Wipe or securely delete data from your mobile device before you dispose of it. Additionally, unlink your Okta Verify MFA.
Notify IT immediately if your Stevens-owned mobile device is lost, stolen, or misplaced. More information on filing a report can be found here.
These best practices should be used for all devices used to connect to Stevens email or systems.
Portable Storage Devices
Best Practices for Portable Storage Devices
Portable Storage Devices refer to components that can be plugged into a system such a computer laptop or digital camera and used to transfer or store digital information or data (e.g., text, video, audio, and/or image data). Examples of portable storage devices include USB thumb drives, memory cards, and external hard drives. Please ensure the following when handling a portable storage device:
Use encryption: Save your data only on encrypted portable storage devices.
Separate personal and business portable storage devices: Do not use your personal portable storage device on Stevens-owned computers to minimize the risk of data breaches and accidental data sharing.
Do not plug an unknown portable storage device into your computer: If you find an unknown portable storage device, give it to the Division of Information Technology. Do not plug it into your computer to see whom it belongs to or what is on it to prevent potential malware infections.
Phishing
Phishing Awareness
What is Phishing?
Phishing is a form of fraud in which a hacker tries to acquire confidential information such as login credentials or account information by masquerading as a reputable entity or person in email, IM, or other communication channels.
What is Spear Phishing?
Spear phishing is attacks directed at specific individuals, roles, or organizations. Since these attacks are so targeted, attackers may go to great lengths to gather specific personal or institutional information in the hope of making the attack more believable and increasing the likelihood of its success.
Why is Phishing awareness important?
When an individual falls victim to a phishing attempt, they often become either infected with malware or have their username and password stolen. Either occurrence can be extremely damaging as personal information such as social security numbers, driver's licenses, or sensitive information related to Stevens' goals and objectives can be disclosed. Also, a skilled attacker can start with a single username and password and escalate their privileges which allow them to acquire critical company information such as financial reports and student data.
How do I report a phishing attempt?
If you receive a suspicious email, please report it to the Office of Information Security.
External Email Tag in Office 365 Email
The external email tag is a new feature that will help you identify emails that originate outside the University’s email systems by prepending a notification to the email message.
Emails tagged external sender notification may come from legitimate external sources and services and should not be discarded without reviewing them first.
Why Is This Notification Added?
Phishing attacks often originate from external sources using deception, email, and website impersonation to steal credentials and other personal information. The external sender notification is just a reminder to use caution when handling emails from external sources.
What Should I Do?
Not all external emails are malicious, but when you see the external sender notification you should be wary about:
Opening attachments
Clicking on links
Providing personal information
Performing financial transactions for the sender
When a sender appears to be someone at the university but has the external sender notification, be extra cautious. Report suspected phishing attempts to the Information Security Office. Click the Report Phishing button in Microsoft Outlook.
Is Email with the External Sender Notification Always External?
Some technology services used by the University that generate emails may show the external sender notification tag, such as Zoom, Box, Google Drive, and Office 365 apps like Teams and One Drive.
My Department’s Email is Getting the External Sender Notification tag
If an email from your departmental email system or vendor bulk email is getting the external sender notification, send an email to [email protected] to request an exception. Include the following information:
Requesting Business Unit: (College, Department, Organization, etc.)
Requesting Point of Contact: Name, Email address, and phone number. (*Should be an individual familiar with the third-party vendor used by unit for mass email communications)
Name of third-party vendor service or system:
Business Process it supports: (Examples: Internal communications, external communications, newsletters, fundraising, etc.)
Audience/Size: (Faulty, Students, Alumni, External Sponsors, etc.)
Frequency of Use: (Ad hoc, daily, weekly, monthly, etc.)
FAQ
Can I personally opt-out of [External] tagging?
No, [External] tagging is added to all Stevens email accounts to help identify email from external sources.
Are [External] tagged messages dangerous?
Not all [External] messages are dangerous. Many legitimate messages come from external sources. However, a common phishing technique is spoofing our Stevens email addresses. The [External] tag is one more mechanism to determine authenticity.
Does [External] tagging do any additional scanning, filtering, or sorting?
No additional scanning, filtering, or sorting is performed. If the message origin is a non-Stevens Email system, then [External] is added to the beginning of the email message subject.
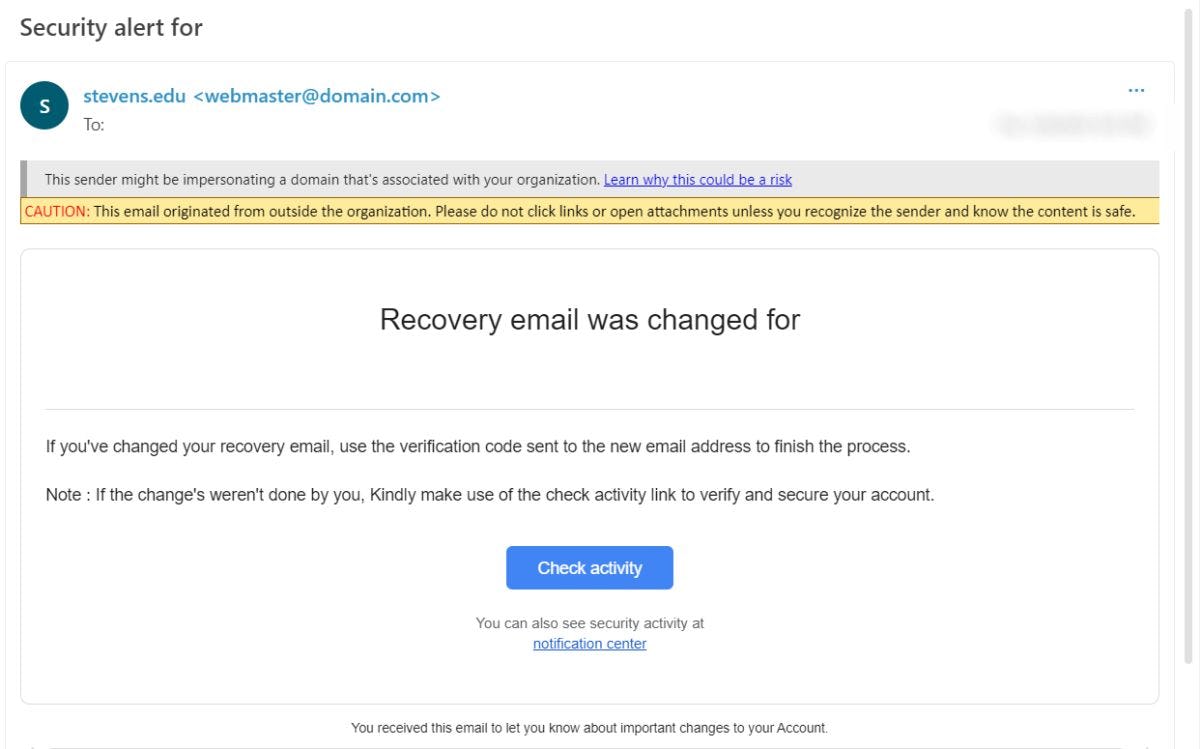
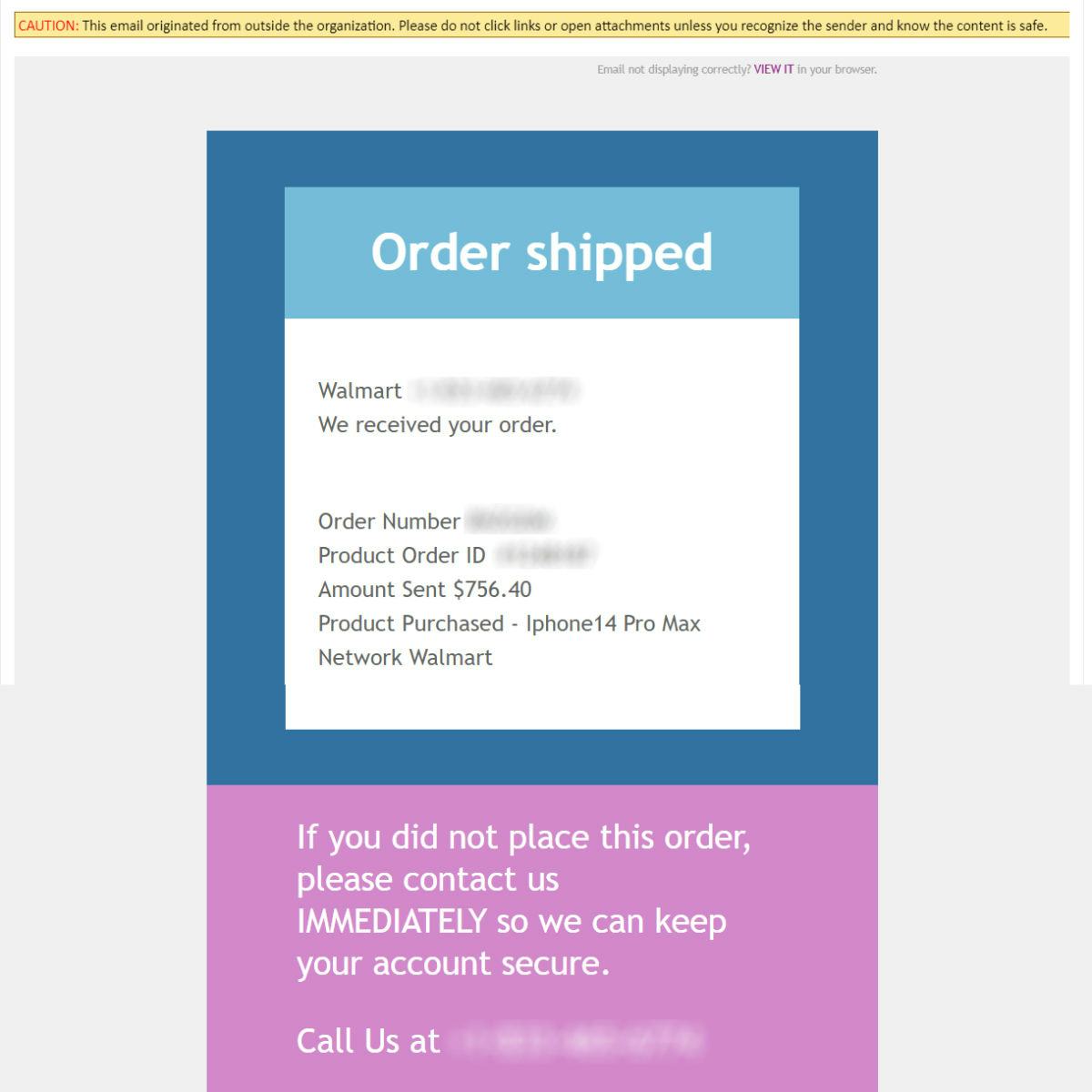
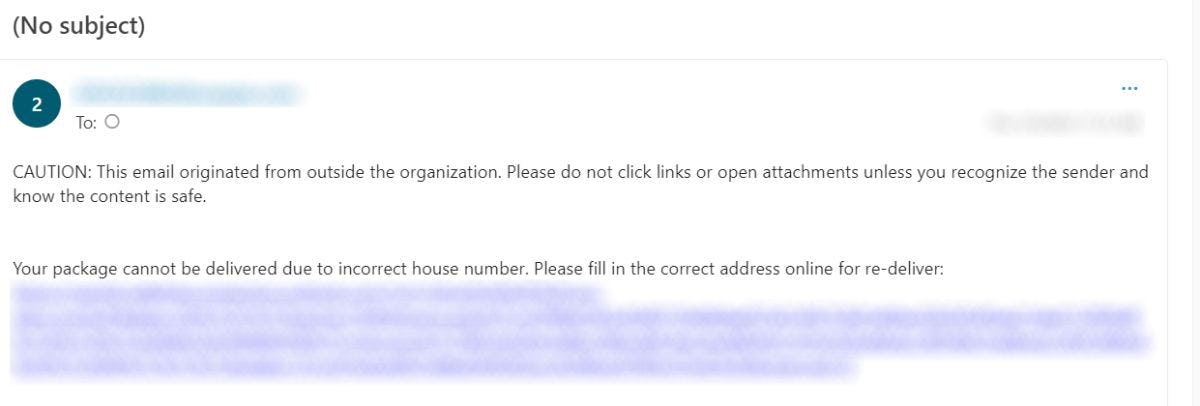
How to Spot Phishing
The email indicates "important" or stresses "Urgency" to increase the likelihood of the recipient clicking the link.
Hovering a mouse over the link produces a different suspicious weblink than what is provided in the email.
The email address displayed is unknown and is not consistent with Stevens messaging formats.
Vaguely worded attachment.
Vague email content requesting the recipient take action. Often malicious emails will direct an individual to click a link or open a file.
Unsolicited email from an unknown source.
Vague email subject.
Vague email content. Note: while some emails do not have an attachment or a web URL to click it should be considered suspicious due to extremely vague content. Hackers will send these emails to discover who will reply and engage in conversation. This is often the first step in a social engineering attempt to discover confidential information.
Phish Bowl
Use this list to see some phishing (fake) emails that have been spotted at Stevens. Below you will find some examples of phishing emails seen on campus. We worked to remove any malicious content from the messages but recommend against interacting with any links or email addresses in the examples. If you get a suspicious email but do not see it listed here, DO NOT assume it is safe. There are many variants of every phish, and new ones are sent each day. When in doubt, consult [email protected].
Report suspected phishing attempts to the Information Security Office. Click the Report Phishing button in Microsoft Outlook.
Warning: Do not explore the links or email addresses in the phishing emails listed here. We work to sanitize these examples, but please do not investigate them further on your own. Still not sure? Read more in our “How to Spot Phishing” section on this page.
Password Tips
Securing Your Password
Passwords are the key to almost everything you do online, and you probably have multiple passwords that you use throughout the day. Choosing hard-to-hack passwords and managing them securely can sometimes seem inconvenient. Fortunately, there are simple ways to make your passwords as secure as possible. Doing so can keep hackers from taking over your accounts and prevent theft of your information (or money from online banking!).
These 8 tips will help make your digital life more secure. 8 Tips to Help Make Your Digital Life More Secure
Change your password often (365 days). If you need to change your Stevens password, you can do so here.
Never reveal your passwords to others. You probably wouldn’t give your ATM card and PIN to a stranger and then walk away. So, why would you give away your username and password? Your login credentials protect information as valuable as the money in your bank account. Nobody needs to know them but you—not even the IT department. If someone is asking for your password, it’s a scam. See Smart Alternatives to Password Sharing.
Use different passwords for different accounts. That way, if one account is compromised, at least the others won’t be at risk.
Use multi-factor authentication (MFA). Even the best passwords have limits. Multi-Factor Authentication adds another layer of protection in addition to your username and password. Generally, the additional factor is a token or a mobile phone app that you would use to confirm that you are trying to log in. Learn more about MFA and how to turn it on for many popular websites at https://www.turnon2fa.com/.
Length trumps complexity. The longer a password is, the better. Use at least 16 characters whenever possible.
Make passwords that are hard to guess but easy to remember. To make passwords easier to remember, use sentences or phrases. For example, “breadandbutteryum”. Some systems will even let you use spaces: “bread and butter yum”. Avoid single words, or a word preceded or followed by a single number (e.g. Password1). Hackers will use dictionaries of words and commonly used passwords to guess your password. Don’t use information in your password that others might know about you or that’s in your social media (e.g. birthdays, children’s or pet’s names, car model, etc.). If your friends can find it, so will hackers.
Complexity still counts. To increase complexity, include upper and lower case letters, numbers, and special characters. A password should use at least 3 of these choices. To make the previous example more secure: “Bread & butter YUM!”
Use a password manager. Password management tools, or password vaults, are a great way to organize your passwords. They store your passwords securely, and many provide a way to back-up your passwords and synchronize them across multiple systems. One such password manager is LastPass, which will fill out passwords in your browser for you and generate new ones when you change your password. For more information on LastPass, see LastPass FAQ.
Need IT Support?
Get support through our self help resources, contacting IT support or visiting TRAC.