Through Pioneering “Fuzzing” Techniques, Stevens Researcher Makes Clear Progress Against Cyberattacks
NSF funding supports efforts to boost the security of software used every day, everywhere
Jun Xu, assistant professor of computer science at the Charles V. Schaefer, Jr. School of Engineering and Science at Stevens Institute of Technology, spends his days hacking into software.
But Xu is not phishing for funds for that elusive Nigerian prince, or accumulating a network of zombie computers poised for malware attacks. Quite the opposite —he’s working to outsmart malicious hackers by improving the methods used to uncover code vulnerabilities in the software most of us rely on every day. The National Science Foundation (NSF) recently awarded a $1.2 million grant to Xu and co-Principal Investigator Long Lu of Northwestern University to continue these efforts.
What’s the buzz about fuzz?
“Vulnerabilities are the fundamental stress to software security,” Xu said. “In 2017, the WannaCry attack infected millions of computers and caused billions of dollars in losses worldwide, and it was all due to ransomware that encrypted every file on the infected machine and demanded a ransom in Bitcoins to recover the data. The bad guys exploited the vulnerabilities in the Microsoft Windows operating system to plant the ransomware. To completely solve the problem of cybersecurity, we have to handle the vulnerabilities in our increasingly large and complex software systems.”
His NSF project, “Collaborative Research: Secure and Trustworthy Cyberspace (SaTC): CORE: Medium: Rethinking Fuzzing for Security,” aims to do just that, in some groundbreaking ways.
If you’re a little fuzzy on fuzzing, you’re probably not a software security expert. Fortunately for all of us, Xu is.
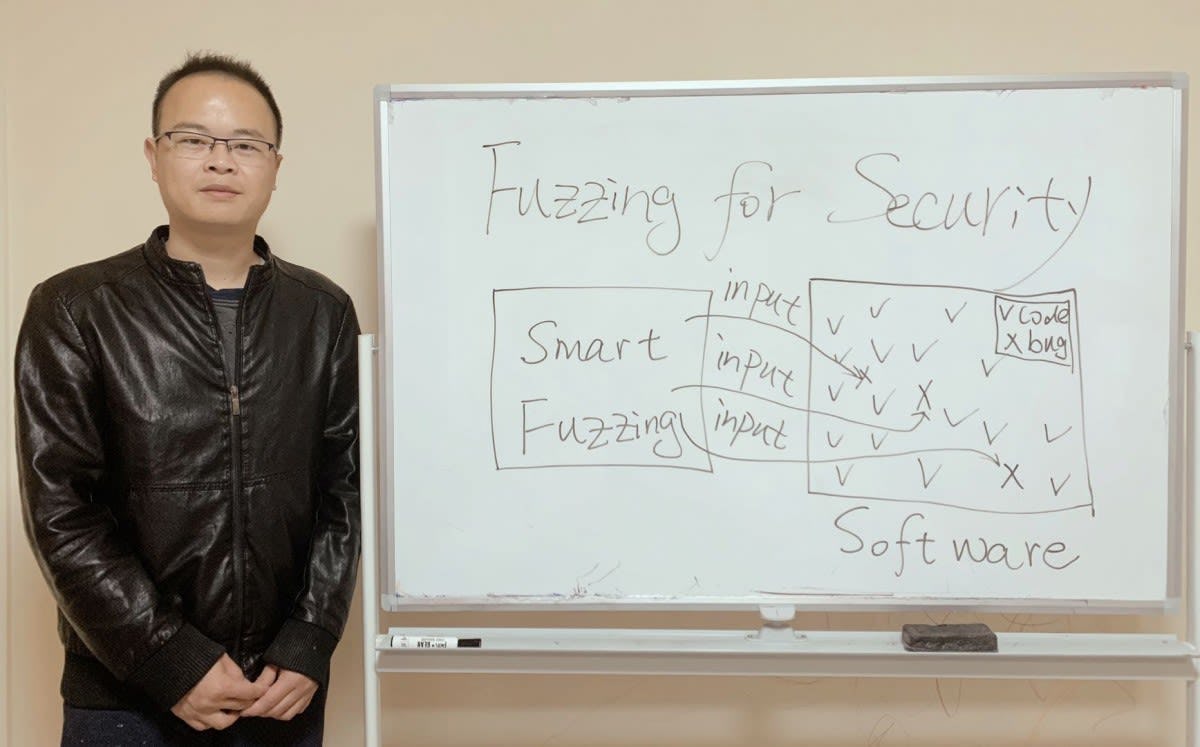
“Fuzzing is a popular technique to find hidden vulnerabilities in software such as email and PDF readers that we all use in our daily lives,” he explained. “The philosophy of fuzzing is simple. Software takes input such as typing text or clicking a mouse, draws on that input, and gives output. Fuzzing generates random, unexpected inputs, then checks if those inputs create an abnormal state or a crash in the software, to unveil or trigger hidden vulnerabilities.”
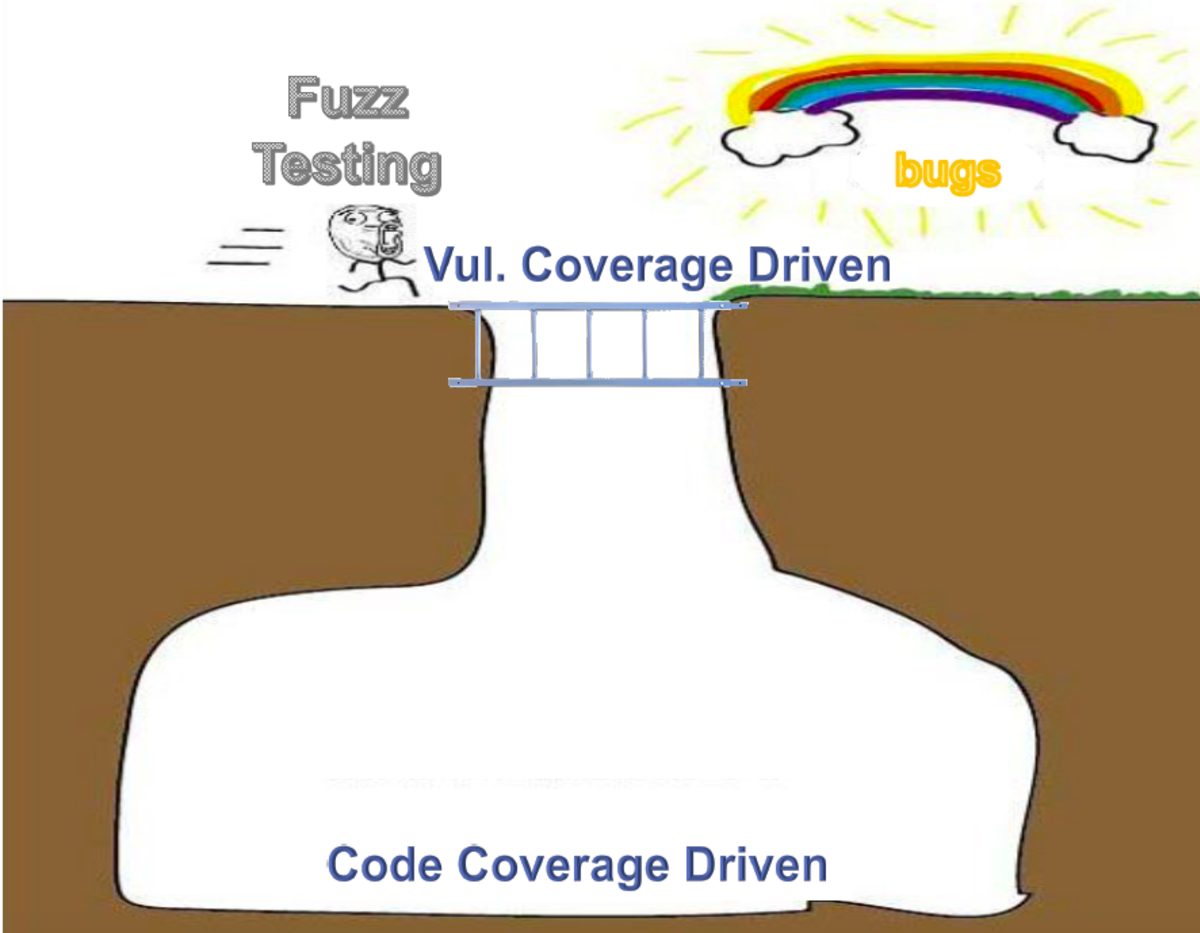
Traditionally, this process has focused on code-coverage-driven fuzzing, which generates a lot of input to cover as much code as possible, regardless of whether the code contains vulnerabilities. In contrast, Xu is developing vulnerability-coverage-driven fuzzing, a potentially stronger approach that seeks to first find code that actually contains vulnerabilities, and then trigger as many of those vulnerabilities as possible. It’s a fine distinction, but one that could finally start to make cyberattacks extinct.
Xu first looks at all the code in the software, then conducts a program analysis to estimate the distribution of the vulnerabilities in that code. At that point, the code is split into regions based on where vulnerabilities are located. Next, he creates and mutates inputs to reach the code only in those at-risk regions and, most importantly, trigger the vulnerabilities hidden there.
“Covering every region of the code with random end-codes is not enough, because there’s no guarantee you’ll trigger vulnerabilities,” Xu said. “Vulnerability-coverage-driven fuzzing is an intuitive technique that could ultimately make our testing smarter and more targeted, so we can find the vulnerabilities and better secure all kinds of software.”
“Combining theories and practice to solve real-world problems”
Xu’s work could potentially impact most things you do throughout your day —including reading this article on your computer.
“All the software running on our desktops and laptops can be attacked,” Xu said. “Using our vulnerability-coverage-driven fuzzing, we can more effectively and efficiently discover and remove the software code vulnerabilities that hackers use to exploit to get unauthorized access. When we reduce the attack surfaces, we reduce the chance that your computer will be attacked.”
And for Xu, that’s what it’s all about.
“I love computer science because we’re combining theories and practice to solve real-world problems,” he said. “My career goal is to completely solve the problems of software security, and I’m excited that this NSF-funded project will bring tremendous help to the general public. At Stevens, we have access to the right undergraduate and graduate students to support this research, the proximity to New York City to build collaborations with tech companies in the security industry, and the computational powers and preliminary funding and resources to make it happen.”
But Xu also stresses that ensuring expert cybersecurity isn’t confined to the experts.
“Everyone should pay attention to software security and software vulnerability,” Xu said. “When you receive notifications to update your software, in many cases, it’s to patch software vulnerabilities, so it’s important that you do every software update.”
Learn more about computer science at Stevens: